 Arkose is a set of tool to make sandboxing desktop application easy.
Arkose is a set of tool to make sandboxing desktop application easy.It basically lets you start any installed binary in a configurable
container. You can choose how much disk space you want to give it, if
it should have network access and if it should be able to access your
/home.
Changes are stored through copy-on-write using aufs2, so the sandboxed
application won't notice it's not running directly on your computer but
you'll be protected from most harm it could make.
Arkose is currently made of:
- arkose: Command line utility with C helper
- arkose-gui: GUI for integration in the gnome desktop (Similar to the Run dialog)
- arkose-nautilus: Nautilus integration
- arkose-wrapper: Wrapper for regular apps to have them start in a container
It basically lets you start any installed binary in a configurable container. You can choose how much disk space you want to give it, if it should have network access and if it should be able to access your /home.
Changes are stored through copy-on-write using aufs2, so the sandboxed application won't notice it's not running directly on your laptop but you'll be protected from most harm it could make.
Download.
- arkose: Command line utility with C helper
- arkose-gui: GUI for integration in the gnome desktop (Similar to the Run dialog)
- arkose-nautilus: Nautilus integration
- arkose-wrapper: Wrapper for regular apps to have them start in a container
It basically lets you start any installed binary in a configurable container. You can choose how much disk space you want to give it, if it should have network access and if it should be able to access your /home.
Changes are stored through copy-on-write using aufs2, so the sandboxed application won't notice it's not running directly on your laptop but you'll be protected from most harm it could make.
Download.
Latest version is 1.3.3
released on 2011-09-15
Some bugs have also been fixed:
Sadly one feature didn’t make it in time for Feature Freeze, that’s the advanced firewalling in filtered network mode. I’ll probably be working on it on the side and push it to a 1.4 branch that’ll be used for Oneiric+1.
I’ll now mostly be focusing on bugfixes for the remaining of the cycle and polishing some of the existing features. So please, test it and file bugs!
If you want to help with the translation effort, you can go translate Arkose on Launchpad or just send me a .po and I’ll do it for you.
For these who want to run the current upstream code, get the bzr branch:
bzr branch lp:arkose
The new features are:
Some bugs have also been fixed:
- Make the Global Menu integration (dbusmenu) work with Ubuntu Oneiric
- Update the test suite
- Fix arkose-cli’s help to be a lot more accurate
- Restrict LXC’s configuration to the bare minimal
- Use point-to-point network configuration in filtered mode (rather than a /30 per container)
- Make sure everything in the container gets properly killed on exit
- Fix Arkose to handle command line parameters properly (instead of just ignoring them)
Sadly one feature didn’t make it in time for Feature Freeze, that’s the advanced firewalling in filtered network mode. I’ll probably be working on it on the side and push it to a 1.4 branch that’ll be used for Oneiric+1.
I’ll now mostly be focusing on bugfixes for the remaining of the cycle and polishing some of the existing features. So please, test it and file bugs!
If you want to help with the translation effort, you can go translate Arkose on Launchpad or just send me a .po and I’ll do it for you.
For these who want to run the current upstream code, get the bzr branch:
bzr branch lp:arkose
The new features are:
- Filtered network support (one interface per container, routed/firewalled)
- Video devices passthrough (useful for Skype)
- Support bind mount of files (thanks to Colin Watson)
- Reworked UI for the wrapper
- All the UIs and CLIs now support translation with an initial (rough) french translation already available.
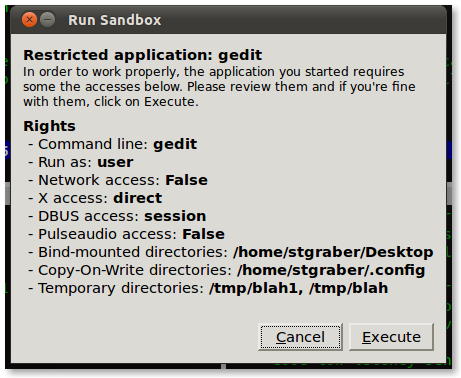
- DBUS filtering is now included in Arkose and available through the wrapper. The gedit example profile is using it.
- It’s now possible to temporarily modify a wrapper profile before starting it.
- Device support has been changed to no longer be limited to /dev/video* devices.

How do I verify a download?
There are two ways to check the files you've downloaded from a project:
The difference between the two is that the MD5 lets you check the file hasn't changed between leaving Launchpad and arriving on your machine, whereas the signature lets you check that the file hasn't changed since it was signed.
- using the MD5 sum that Launchpad generates
- optionally, using the digital signature generated if the uploader signed the file.
Using the MD5 sum
When a project maintainer uploads a file that they want to make available for download, Launchpad analyzes the file using the MD5 hashing algorithm. This produces a short sequence of letters and numbers.
You can use that sequence, called the MD5 sum, to check that the file has arrived on your machine intact.
Step 1: Get the MD5 sum by following themd5link next to the file you've downloaded.
Step 2: Open a terminal, enter the directory where you downloaded the file and type:
md5sum filename
Obviously you need to replace filename with the name of the file you downloaded.
Step 3: You'll see an MD5 sum. Check that it's the same as the one you obtained in step 1. If the two sums are different, there has been a problem downloading the file. You should delete the file and try downloading it again. Do not use the file if the MD5 sums do not match.
Verifying a signature
When a project maintainer uploads a file to Launchpad, they have the option of also digitally signing the file and uploading the resultant signature.
You can tell which files have a signature by looking out for the sig link alongside the md5 link. Verifying the files signature lets you check that the file is exactly as intended by whoever signed the file.
Step 1: Download the signature file to the same directory where you've downloaded the project file you want to verify. The signature file will have the same name as the project file you've downloaded but with .asc or .sig appended to the end.
Step 2: Open a terminal, change to the directory where you have saved the file and accompanying signature, then enter the following:
gpg --verify signaturefilename
Replace signaturefilename with the signature's filename.
gpg will now try to check the signature against the signer's public key. If your version of gpg is configured to retrieve public keys automatically, you can skip to step 4. Otherwise, you'll need to fetch the signer's public key manually.
Step 3: If gpg can't find the public key on your local system, it will give you an error message similar to this:
gpg: Signature made Sun 28 Jun 2009 02:20:52 BST using DSA key ID 2F9532C8
gpg: Can't check signature: public key not found
That's no problem: you can easily retrieve the public key. Simply copy the key ID; it's the alphanumeric code,2F9532C8, at the end of the first line of the error message.
Next, enter:
gpg --recv-keys 2F9532C8
gpg will now pull down the public key and you can re-rungpg --verify signaturefilename
Step 4: We're nearly done! You'll see a message from gpg that is similar to this:
gpg: Signature made Sun 28 Jun 2009 02:20:52 BST using DSA key ID 2F9532C8
gpg: Good signature from "Guillermo Gonzalez < guillermo.gonzalez@canonical.com>"
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: CDD8 87C2 C5CE CD1A C593 8EEF 698A D97E 2F95 32C8
This message shows that the file hasn't changed since it was signed by the uploader. Because Launchpad allows only a project's owners and series release managers to upload files for download, you may decide that this is enough confirmation that the file is good.
However, you can verify that the public key is owned by someone that you trust from the project.
Step 5: Visit Launchpad's people search page and search for the person name in the output fromgpg --verify.
From their profile page, you can check their involvement in the project and also that they own the key used to sign the file you downloaded.
If you liked this article, subscribe to the feed by clicking the image below to keep informed about new contents of the blog:










0 comments:
Post a Comment